Archive for June 2016
Teardrop Attack : What Is It And How Does It Work?
Teardrop attack is a type of Denial of Service (DoS) attack which
exploits the fragment offset field in the IP header to produce buggy fragments
which are then delivered to the target machine. Unable to rearrange the
fragments, the victim keeps on accumulating the fragments until it crashes.
As the
name suggests, the Teardrop Attack works gradually by sending the fragmented
packets to a target machine. It’s a type of a denial-of-service (DoS) attack which overwhelms the target machine with the
incomplete data so that the victim crashes down.
In Teardrop Attack, fragmented packets that
are sent in the to the target machine, are buggy in nature and the victim’s
machine is unable to reassemble those packets due to the bug in the TCP/IP
fragmentation.
In
this way, the packets keep on getting accumulated over the victim’s machine and
finally due to the buffer overflow, the target machine crashes down.
How Teardrop Attack works?
Here, I am taking a
reference from the Juniper’s technical publication to illustrate how does it
work —
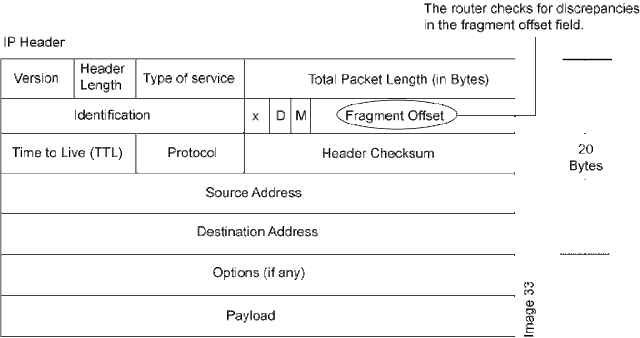
As
you can see in the above figure of IP header, which operates at the network layer, there is
a field called fragment offset field.
Teardrop Attack and Fragment Offset:
Understand it like this — When a large amount
of data is sent across the internet, the data is broken into the smaller
fragments. Each of these fragments is assigned a number. When they reach
the receiving end, these fragments are rearranged to reproduce the original
data or message.
To identify the sequencing of the fragments,
the fragment offset field holds the necessary information using which the
target machine rearranges the sequence.
However, in the Teardrop Attack, the fragment
offset field is made buggy by the hacker so the victim’s machine is unable to
find the relative fragments.
So, as the name suggests, the buggy packets
keep on accumulating at the victim’s side like teardrops and ultimately it
leads to the machine crash.
However,
modern networking devices can
detect this discrepancy in a fragmented packet. Once they detect the problem,
they simply drop the packet.
For More Details Contact :
Redback IT Academy
#AL 24 , TNHB Phase III,
Sathuvacheri
Vellore.
Contact : +91 8189985559
Top 10 Common Hacking Techniques You Should Know About
Using
simple hacks, a hacker can know about your personal unauthorized information
which you might not want to reveal. Knowing about these common hacking
techniques like phishing, DDoS, clickjacking etc. could come handy for your
personal safety.
Unethical
hacking can be called an illegal activity to get unauthorized information by
modifying a system’s features and exploiting its loopholes. In this world where
most of the things happen online, hacking provides wider opportunities for the
hackers to gain unauthorized access to the unclassified information like credit
card details, email account details, and other personal information.
So,
it is also important to know some of the hacking techniques that are commonly
used to get your personal information in an unauthorized way.
1. Keylogger
Keylogger
is a simple software that records the key sequence and strokes of your keyboard
into a log file on your machine. These log files might even contain your personal
email IDs and passwords.
Keylogger
is one of the main reasons why online banking sites give you an option to use
their virtual keyboards.
2. Denial of Service (DoS\DDoS)
A
Denial of Service attack is a hacking technique to take down a site or server
by flooding that site or server with a lot of traffic that the server is unable
to process all the requests in the real time and finally crashes down.
For
DDoS attacks, hackers often deploy botnets or zombie computers which have got
the only work to flood your system with request packets.
3. Waterhole attacks
If
you are a big fan of Discovery or National Geographic channels, you could
relate easily with the waterhole attacks. To poison a place, in this case, the
hacker hits the most accessible physical point of the victim.
For
example, if the source of a river is poisoned, it will hit the entire stretch
of animals during summer. In the same way, hackers target the most accessed
physical location to attack the victim. That point could be a coffee shop, a
cafeteria etc.
Once
hackers are aware of your timings, they might create a fake Wi-Fi access point
and modify your most visited website to redirect them to you to get your
personal information.
4. Fake WAP
Even
just for fun, a hacker can use software to fake a wireless access point. This
WAP connects to the official public place WAP. Once you get connected the fake
WAP, a hacker can access your data, just like in the above case.
5. Eavesdropping (Passive Attacks)
Unlike
other attacks which are active in nature, using a passive attack, a hacker just
monitors the computer systems and networks to gain some unwanted information.
The
motive behind eavesdropping is not to harm the system but to get some information
without being identified.
6. Phishing
Phishing
is a hacking technique using which a hacker replicates the most-accessed sites
and traps the victim by sending that spoofed link.
Once
the victim tries to login or enter some data, the hacker gets that private
information of the target victim using the trojan running on the fake site.
7. Virus, Trojan etc.
Virus
or trojans are malicious software programs which get installed into the
victim’s system and keeps sending the victims data to the hacker.
8. ClickJacking Attacks
ClickJacking
is also known by a different name, UI Redress. In this attack, the hacker hides
the actual UI where the victim is supposed to click.
In
another word, the attacker hijacks the clicks of the victim that aren’t meant
for the exact page, but for a page where the hacker wants you to be.
9. Cookie theft
The
cookies of a browser keep our personal data such as browsing history, username,
and passwords for different sites that we access. Once the hacker gets the
access to your cookie, he can even authenticate himself as you on a browser.
10. Bait and switch
Using
bait and switch hacking technique, the hacker runs a malicious program which
the user believes to be authentic. This way, after installing the malicious
program on your computer, the hacker gets unprivileged access to your computer.
To Learn Hacking :
Contact
us : Redback IT Solutions Private Limited
#AL – 24 TNHB Phase III,
Sathuvacheri,
Vellore.
Call
us : +91 8189985551
Mail
us : training@redbacks.in